IIT Delhi's fatal liability
How secure is IIT Delhi from Man-in-the-middle attacks?
I’m publishing this 6 months after privately emailing IITD sysadmin notifying them about a critical vulnerability, to have them fix it properly.
Facts
- The institute asks its users to install a CA certificate issued by itself to secure internal communications
- The official download link for the CA certificate is hosted on an unencrypted plain HTTP page
SSL certificates and MITM attacks
Before we continue, let’s understand how SSL (CA) certificates work (source).
- A browser attempts to connect to a website (i.e. a web server) secured with SSL. The browser requests that the web server identify itself.
- The web server sends the browser a copy of its SSL certificate.
- The browser checks to see whether or not it trusts this SSL certificate. If so, it sends a message to the web server.
- The web server sends back a digitally signed acknowledgment to start an SSL encrypted session.
- Encrypted data is shared between the browser and the web server.
Focus on the 3rd step.
The browser checks to see whether or not it trusts the SSL certificate.
How?
Our computer comes with a small list of certificates pre-installed with the operating system. They are called Trusted Root Certificates and belong to organizations called Certificate Authorities (CA). The CAs have the authority to digitally sign a web server’s certificate implying to the world that they trust it. Thereby, the following chain of trust is formed —
- You trust the browser
- Browser trusts the OS
- OS trusts the CAs
- CAs trust their root certificates
- Any one of the root certificates trusts the web server’s certificate
And this is how the browser ultimately trusts a web server. Looks pretty simple, right? Yes, indeed. However, this simplicity comes with a very interesting and challenging possibility.
What if one of those root certificates belong to a malicious actor?
In that case, it’s game over! All the communication between your computer and any other web server is compromised, even if it happens over HTTPS.
- A malicious actor installs his bad certificate as a trusted root on your computer.
- You send a request to any web server. Cerficate exchange is about to begin.
- Malicious actor intercepts the request and pretends to be the said web server and responds with his certificate. Since his certificate is already present on your system, you trust it.
- He also initiates another connection with the web server pretending to be you.
- All further communcations between you and the web server go through him.
The malicious actor is sitting in the middle of you and the web server, and neither of you knows about it. This is called a Man in the middle (MITM) attack and it is one of the most dangerous ones out there.
Back to IIT Delhi
Since the official link to download the CA certificate is published on a plain HTTP page , anyone can inject a malicious link instead. The content of this page can also be modified to show modified SHA1 & MD5 hashes. An uninformed user will follow that link to download the malicious certificate and install it as a Trusted Root on his machine compromising all of his future communications.
Vulnerability reporting
I sent the following email to the sysadmin sharing my concerns on Nov 29, 2018.
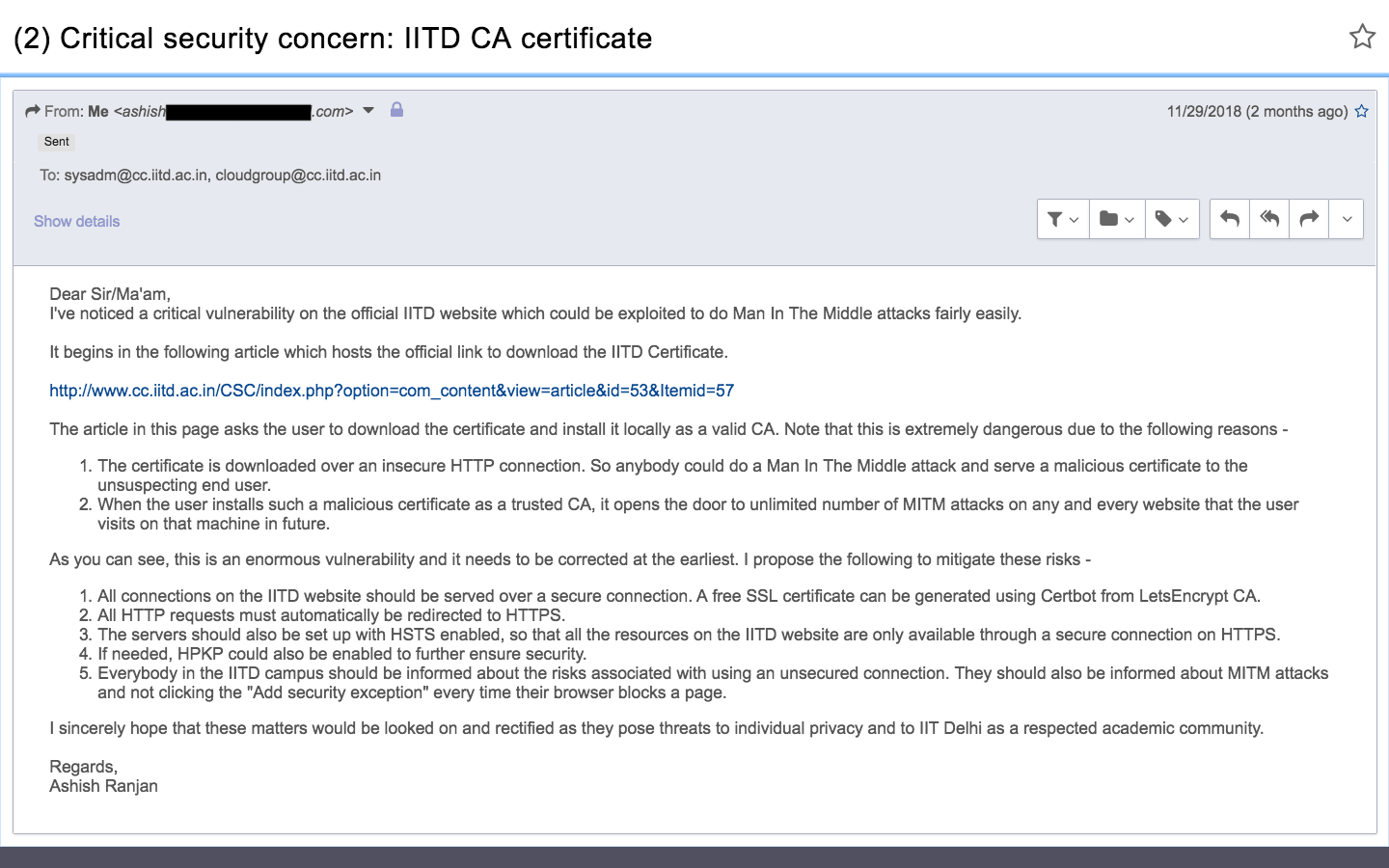
Response
I received no response. However, the relevant page was updated accordingly on Nov 30, 2018 (within a day), with the following changes —
- The download link was migrated to HTTPS
- SHA1 and MD5 fingerprint hashes added
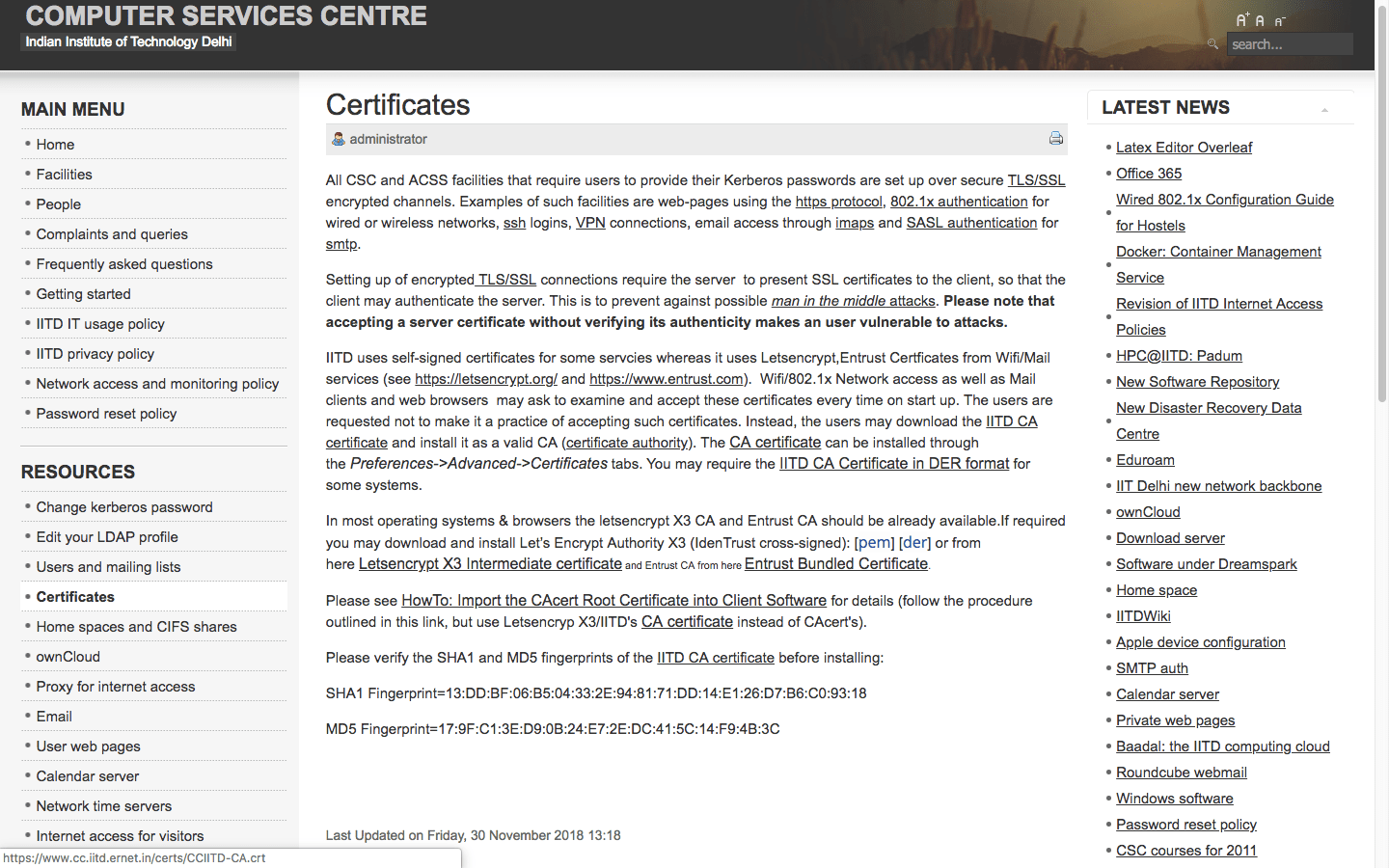
Existing issue
Although the certificate download link has been migrated to HTTPS, the page on which it is hosted is still served on plain HTTP. A grave vulnerability, as explained above.
Proposals
- All connections on the IITD public website should be served over HTTPS. A free SSL certificate can be generated using Certbot from LetsEncrypt CA.
- All HTTP requests must automatically be redirected to HTTPS.
- The servers should also be set up with HSTS enabled, so that all of the IITD resources are only available over HTTPS.
- Fingerprints — Since SHA1 and MD5 aren’t secure , SHA2 should be used instead.
- Everyone in the IITD campus should be informed about the risks associated with using an insecure connection.
Conclusion
It is still fairly easy to do everlasting MITM attacks inside IIT Delhi campus. Since most of the users have no idea about this issue, the ensuing disaster would be enormous. IIT Delhi should follow other IITs such as Kanpur, Madras , Roorkee who serve their pages over HTTPS.